Experts say Dito Telecommunity can allow China to mine data of Filipinos, and the Philippine military would be helping it by letting the telco build cell sites in its camps and bases

AT A GLANCE
- By allowing a China-backed telco to build cell sites in its camps and bases, the Philippine military may become an accessory to China mining Filipinos’ data, independent experts said.
- The military’s conclusion that its co-location deals with telcos are low-risk is inaccurate, and its analysis, insufficient.
- The mitigating measures the military relies on are basic and entry-level, making it an “open gate” for cyber attacks.
- China has a long and rife history of cyber espionage, and the military appears to discount this by going ahead with its deal with the 3rd telco.
If the Chinese government-backed Dito Telecommunity meets its targeted market share, 3 out of every 10 smartphone-wielding Filipinos might have China’s ears directly listening in on their conversations.
However, those 3 Dito subscribers won’t only be talking to Dito clients. Their phone, text, and online conversations will certainly involve Globe and Smart subscribers – basically, everyone else.
Those conversations will be transmitted through the airwaves by Dito’s cell sites placed alongside those of the other two telcos on communication towers, many of which will be located in camps and bases of the Armed Forces of the Philippines (AFP) all over the country.
Here's the reality: China has reclaimed 7 natural reefs in the West Philippine Sea and turned them into artificial islands, and built military bases on them. Chinese ships of different kinds prowl Philippine seas, inching ever closer to its shores and driving Filipino fishermen away from their own waters.
China sells Filipinos fish it caught in the Philippines. It is sending its workers to take up jobs and residence in the Philippines. China has a long list of loans it offers the Philippine government, and many deals with Philippine companies, to build dams, bridges, airports, railways, expressways, and other megalithic projects to be built by Chinese employees of Chinese companies.
What else could China export to the Philippines? What else could it get Filipinos to buy or pay for? How could it get Filipinos to open up and ignore threats to their own freedoms and opportunities?
Easy. It can look at what every Filipino is talking about online and on their phones, and the information they share on social media, to study their habits and tendencies.
Data access leads to control
“Once we give up data to any other country, we give up sovereignty, right? When we give up data, we give up control. That’s the fundamental issue with all of this stuff,” said an expert working on cybersecurity with artificial intelligence (AI) in the Philippines, after reading the military’s risk analysis of its cell sites deal with the China-backed Dito Telecommunity, formerly known as Mislatel.
(READ: Experts warn of spying risk in AFP deal with China-backed telco)
The cybersecurity expert, who spoke to Rappler on condition of anonymity, also said, “If you have data about somebody, you can influence them, subconsciously, and in different ways. That’s control. Data is always going to be about control.”
He believes the incoming 3rd telco will give the Chinese government wholesale access to Filipinos’ data, and the agreement letting it put up communication equipment inside military camps and bases means the AFP itself would be an accessory to giving up sovereignty over Filipinos’ data.
Quite ironic for an institution mandated to guard national security and sovereignty.
“To simplify this, we’re going to be defending Chinese property with our military, and that’s crazy,” he said.
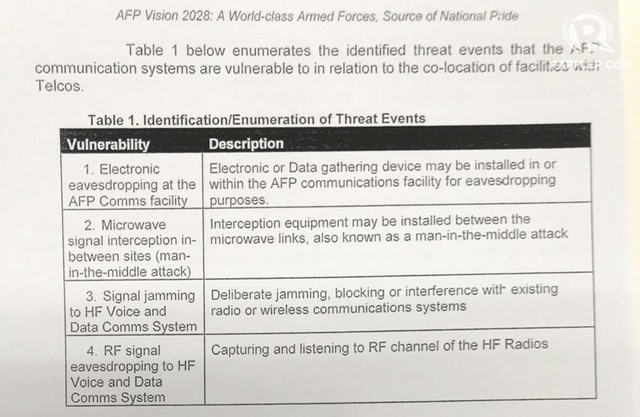
SECURITY THREATS. In its risk analysis, the military identifies vulnerabilities in its communication systems that telcos, particularly China-backed Dito Telecommunity, may exploit through cell sites installed on military properties. Photo sourced by Rappler
What did the risk analysis say?
The risk analysis, conducted by the AFP Office of the Deputy Chief of Staff for Communication, Electronics and Information Systems (J6), confirms that the presence of telco equipment in AFP camps and bases provide an opportunity to exploit several vulnerabilities in the military’s communication systems, namely:
- Electronic eavesdropping at the AFP communications facility
- Microwave signal interception in-between sites (man-in-the-middle attack)
- Signal jamming of the AFP high frequency radio voice and data communication system (AFP-HF)
- Radio Frequency (RF) signal eavesdropping on the AFP-HF
These threats are present in the arrangements with all 3 telcos, but Dito presents a more imminent risk because of its connection to the Chinese government.
In its analysis, the AFP J6 found that most of these threats were highly likely to occur, and that they would almost certainly result in adverse impacts to the military if they do.
Only the threat of a man-in-the-middle attack on the AFP’s microwave-based Fixed Communication System (FCS) was deemed “moderate” in terms of how likely it is to happen, and “high” – as opposed to “very high” – on how certain it is to adversely impact the military should it occur.
In short, the AFP admitted that the telcos, particularly Dito, would probably attempt to exploit the vulnerabilities in its communication systems, and if they do, would have dire consequences.
But then the military said “existing control measures” offset the risks from the threats, however imminent.
“On all 4 threat areas…the AFP determined that the risk to the organization is low, considering that the adopted physical, procedural, and systemic security measures were deemed effective to counter the said threat vulnerabilities,” the analysis stated.
It’s a hasty conclusion, the cybersecurity expert told Rappler, adding, “Anything that deals with data is, by essence, high-risk. Clearly, they want to come to the conclusion that it’s low-risk.”
The military should have ticked “high” likelihood and “very high” adverse impact on all of the threat events, a telco information security practitioner of more than 30 years told Rappler. He, too, requested anonymity.
And instead of brushing off the risks as “low,” the military should have at least considered them to be “medium” or “moderate.”
“The AFP, being a military organization, must assume the maximum risk as a precaution. We are talking here of national security in general, the protection of the right and life of every Filipino,” the telco expert said.
The AFP should have performed “the highest level or most complicated test and vulnerability assessment” possible, he added, because all it takes is one successful hacking attempt to bring an entire system down.
The 7-page risk analysis did not indicate exactly how the AFP J6 gauged the effectiveness of the mitigating measures it said were in place – whether it ran actual tests or merely judged based on theory.
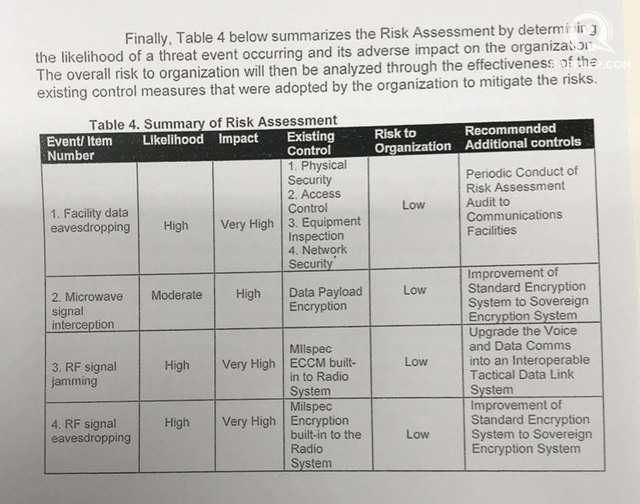
LOW-RISK? The AFP concludes that despite the high likelihood of spying threats to its communication systems, the net risks to the organization are low because of existing control measures. Photo sourced by Rappler
Mitigating measures
The military’s “existing control measures” to mitigate spying risks are mainly to restrict access to the cell sites, inspect pieces of equipment brought in by the telcos and vet their personnel who would install them, encrypt messages sent over microwave or radio transmissions, and a “Network Monitoring System” to guard against attacks.
Besides the existing measures, the AFP J6 recommended “additional controls” that the military did not yet have:
- Periodic conduct of risk assessment audit of communication facilities
- Improvement of standard encryption system into sovereign encryption system
- Upgrade the [AFP-HF Radio] Voice and Data Communications system to an interoperable Tactical Data Link system
Considering that the AFP has had telco cell sites inside its camps and bases since 1998, shouldn’t it have been running periodic risk assessments of the impact of the telcos’ presence on its own information security?
“These agreements have been periodically reviewed and updated, considering the advancement of communication technology infrastructure,” the risk analysis stated. It appears that “periodic review” did not include risk analysis.
In fact, it seems the military did not run a proper risk analysis before drafting and approving the contract with Dito, its Chinese links notwithstanding, because the document Rappler obtained refers to the signing of the contract on September 11, 2019, in the past tense.
When a Senate panel asked for a risk analysis of the deal during a budget hearing for the Department of National Defense on September 30, 2019, Defense Secretary Delfin Lorenzana and the military generals who accompanied him could not produce any.
Lorenzana was abroad on official business when the deal was signed, and he came under pressure to justify why he would sign it himself, or else reject it if he thought the senators' concerns were valid.
The risk analysis Rappler obtained came several weeks after that hearing, during which Lorenzana agreed to delay giving his final approval of the deal until after the Senate reviews it.

PAST TENSE. This paragraph from the first page of the risk analysis refers to the signing of the contract between the military and Dito Telecommunity in the past tense, meaning the document was produced after the deal was already sealed. Photo sourced by Rappler
Standard to sovereign encryption
Encryption means turning an electronic message into a code that, ideally, only the intended receiver can decode and comprehend. The security of that message then depends on the degree of the complexity of the code. The harder it is to crack the encryption code, the more difficult it is to hack that communication.
Because hackers never rest, it is always only a matter of time before they are able to crack even the toughest codes, which is why defenders of secure communications constantly upgrade their encryptions.
The shift from standard to sovereign encryption that the AFP J6 recommends in the risk analysis is urgently needed, and it bears asking why it has not been done sooner.
The government has already allotted P1.5 billion for the military’s Encryption System Development Project under Horizon 2 of the AFP Modernization Program, the risk analysis states.
From HF radio to Tactical Data Link
A Tactical Data Link (TDL) system would be a step up from the AFP-HF radio-based communication system for field missions and combat scenarios. TDLs are more secure and resistant to jamming than high frequency (HF) radio, which the AFP J6 said is “notoriously susceptible to eavesdropping or interception and radio jamming or interference.”
This is farther up the pipeline, the risk analysis states, still in the “requirement definition stage” of the procurement process.
But how can the AFP expect to get funding for these projects when it claims that the security risks from the cell sites deal with Dito Telecommunity are low?
The military contradicted itself and did itself a disservice by downplaying the spying threats in its risk analysis, because then it would not be able to tell the budget department that there’s an urgent need for the upgrades, the telco veteran told Rappler.
If the risks from the co-location deal really are low, “then there is no need to do further actions in terms of higher level of security risk controls and risk mitigation inside the AFP organization, and therefore there is also no need for more sophisticated security countermeasures to be implemented,” the telco expert said.
“However, the author [of the risk analysis] stated otherwise – that there is a need to implement the AFP [cybersecurity] programs.”
The military is an ‘open gate’
As for the “existing control measures” such as personnel and equipment inspections, standard encryption, and network security, all these are basic and entry-level measures that don’t count for much in terms of detecting and warding off attacks on the AFP’s communications, the telco veteran warned.
In its risk analysis, the AFP J6 did not talk about advanced threat protection, threat detection and response, response capability, network forensics, or threat intelligence – advanced standard contingency measures an organization like the AFP needs to withstand cyber attacks.
Based on what security measures the AFP claimed to have in the risk analysis, it appears the military, like most organizations in the Philippines, only has an “initial phase” capability to respond to threats such as phishing, spamming, and hacking.
“Therefore, having this stage or level of security measures…[the AFP] is still viewed as an ‘open gate’ by security experts, or is still ranked as having the least security measures in place,” the telco expert said.
“I’m more worried about the software than I am about the hardware,” said the other expert Rappler consulted, who works in cybersecurity and AI. “Because all of this is a good analysis on the hardware but the problem is going to come from the software."
“They do a good job of saying who gets into the base and who gets into these facilities but they don’t really talk about how do they measure people hacking their way in.”

HASTY CONCLUSION? Experts disagree with the military's conclusion that its telco cell site deals, especially the one with Dito Telecommunity, pose only low-security risks. Photo sourced by Rappler
You’re dealing with China here, said security analyst Jose Antonio Custodio, a former consultant of the Philippines' National Security Council.
Those attempts to hack into the AFP’s communications won’t just come “once in a blue moon. They will be tested by the Chinese on a daily basis. Aaraw-arawin ‘yan.” (They'll do it every day.)
And instead of building up its cyber defenses, the AFP made it easier for China to break in by signing the agreement with Dito.
“The AFP said that [the deal] is low-risk. Therefore, the existence of risk is there. If that was based on their experience with Globe and Smart, then that low risk may become medium-level or even higher because now, you have a direct Chinese entity,” Custodio added.
Chinese cyber espionage is a huge global concern. Australia, Canada, Japan, New Zealand, the UK, and the US are among countries that have restricted, if not totally banned, the use of Chinese communications technologies, including Huawei, which Globe uses in its systems.
China has long been known to snoop into tech companies to copy their designs, and now that it has become a formidable political and military force, worries about its spying have gone beyond the economic.
US intelligence officials believe China poses a greater espionage threat than any other country, the New York Times reported on December 15.
Chinese intelligence officials have been using social media to recruit assets on a mass scale, another New York Times report said in August.
Because it wants to become the dominant political, economic, and military power in the Asia Pacific, China would have a lot to gain from accessing information about the AFP’s plans and its personnel, Custodio said.
The cybersecurity expert agreed with Custodio. The presence of Dito in military camps would naturally entail increased dealings between personnel from the telco and the AFP, on top of the proximity it would give their communication equipment.
“You’re giving away tendencies. People like me, I can see the tendencies of people, just by looking at their data,” the cybersecurity expert said.
“Surveillance will tell you a lot about operations without even having to know what the operation is. You just have to know who are the persons of interest, and if they start clustering together in a map, you could probably say there’s something going on there,” he added.
And then there are the Philippines’ alliances with powers like the US, Japan, and Australia. These allies could be spooked knowing China could be watching and listening from the AFP’s camps.
A country like the Philippines that’s largely dependent on strategic alliances as a deterrent from external aggression cannot afford to compromise those alliances.
The US is the Philippines’ only treaty ally, and it recently said that alliance covers the West Philippine Sea, which could be a flashpoint of a military confrontation with China.
China could be after information on the US that it could cull from the AFP, Custodio said, and there could be a lot, because the US and Philippine militaries engage in a yearly series of joint exercises and information-sharing on domestic threats.
“You’re bringing the element of compromising your secure communications with your real allies, which the Chinese would want to target….The Chinese will now see if they can use their presence in Philippine military facilities to attempt to eavesdrop on Americans and other international partners of the Philippines,” Custodio said.
This is about freedom
Of course, the risks do not only come from Dito or from China. Governments spy on one another and on companies. Companies spy on one another and on governments.
But why would a government lay down its defenses against a potential intruder?
“It would have been okay if China were an honorable country, but it’s actually claiming our territory. They’re within 12 nautical miles of our territory. We’re going to turn into a vassal state,” Custodio warned.
“This is about freedom,” the cybersecurity expert stressed. – Rappler.com
TOP PHOTO: Could China end up manipulating Filipinos by gaining access to their data through the 3rd telco? And could the Philippine military be an unwitting accessory to this? Photos of soldiers by Jire Carreon/Rappler. Collage designed by Alyssa Arizabal/Rappler.
https://www.rappler.com/newsbreak/in-depth/247364-will-philippine-military-china-unwitting-accessory-data-breach-part-2

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.